
A month full of exciting opportunities and developments! As cybersecurity threats evolve, businesses face increasingly sophisticated challenges, from AI-driven ransomware attacks to the rising prevalence of supply chain and social engineering threats. Inheriti® is at the forefront of addressing these issues, offering innovative solutions that enhance data security and privacy. By leveraging decentralized technologies, Inheriti® is shaping the future of cybersecurity, ensuring that digital legacies remain protected in an increasingly complex and dangerous digital landscape. Let’s dive in!
Securing Your Digital Legacy: How Inheriti® Is Shaping the Future of Cybersecurity
Cybersecurity continues to be one of the most pressing challenges for businesses today, with ransomware attacks emerging as a particularly significant threat. These attacks have become more targeted and devastating, as cybercriminals now leverage AI-driven methods to bypass traditional security defenses, making detection and response increasingly difficult. The financial toll of such attacks is immense, encompassing not only ransom payments but also potential legal costs and lasting damage to a company’s reputation.
Another significant threat is the increasing prevalence of supply chain attacks. Cybercriminals target trusted vendors or partners to gain access to a broad range of data, putting entire networks at risk. Furthermore, social engineering attacks are becoming more common, manipulating human vulnerabilities to gain unauthorized entry into sensitive systems.

The cybersecurity landscape is constantly evolving, shaped by emerging threats and innovations that are transforming defense strategies. A key trend is the growing adoption of Zero Trust Architecture (ZTA), which operates on the principle that no one—whether inside or outside the network—should be automatically trusted. In hybrid IT environments, ZTA mitigates the risk of insider threats and lateral attacks, providing enhanced security and more robust protection for businesses.
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing cybersecurity by empowering organizations to analyze data in real time and detect threats with greater precision. As cybercriminals increasingly utilize AI to automate attacks, businesses must adopt AI-driven security solutions to stay one step ahead.
At the same time, digital identity security is gaining heightened importance. With the rise in identity-based attacks, implementing stronger authentication methods—such as multi-factor authentication (MFA) and decentralized identity solutions—has become crucial for managing access control and reducing vulnerabilities.
Our Approach to Combatting Evolving Cybersecurity Risks
Inheriti® leverages decentralized technologies to protect digital legacies by encrypting and fragmenting sensitive data, such as wills and financial documents (upcoming feature), across multiple locations. This decentralized approach eliminates the risk of a single point of failure, which is common in traditional centralized systems.
Our cybersecurity strategy is built around three core pillars: prevention, detection, and response.
- Prevention: Inheriti® employs a combination of Distributed Ledger Technology, client-based storage, and Hardware Security Modules (HSM) to distribute and protect sensitive data. This ensures that even if one part of the network is compromised, the data remains secure.
- Detection: Our platform utilizes advanced cryptographic techniques to authenticate and verify the integrity of stored data, enabling quick identification of any tampering.
- Response: In the event of a breach, Inheriti®’s decentralized architecture makes it virtually impossible for attackers to reconstruct complete data sets, facilitating rapid recovery and minimizing the overall impact.
Inheriti® offers a robust solution for safeguarding digital legacies, providing individuals and businesses with peace of mind regarding their long-term digital assets.

New Features and Enhancements for a Secure Digital Future
With the latest update, Inheriti® significantly enhances accessibility, flexibility, and usability in digital inheritance and data backup management. The introduction of Free Plans allows users to create secure backup plans at no cost, offering a streamlined single-shareholder setup supported by SafeKey Mobile and designed for individuals seeking an easy entry point into digital asset protection.
While these plans maintain strong security through encrypted storage within the Inheriti® Vault, they differ from Paid Plans by removing blockchain dependencies, simplifying the user experience. In parallel, the rollout of Multiple Merge Authorities addresses critical reliability concerns by enabling multiple trusted individuals to initiate the merging process, thereby eliminating single points of failure and improving organizational support.
Additional improvements include a new structured categorization system for data assets, general system enhancements for performance and security, and infrastructure upgrades to ensure scalability.
Collectively, these features lay a strong foundation for future growth and reaffirm Inheriti®’s position as a leading platform for secure, flexible, and user-friendly digital protection solutions. Future updates, which we are already working on, will continue to refine and expand on these features, ensuring that digital inheritance and backup plans evolve with the needs of users worldwide.
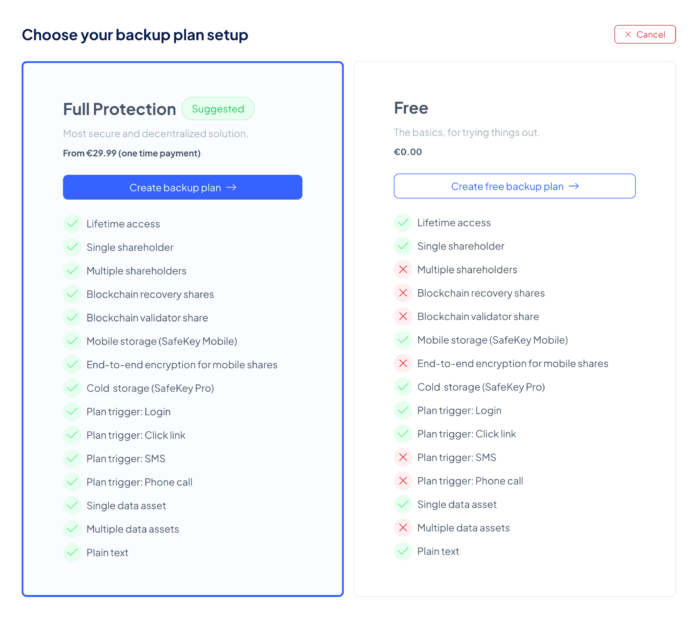
New Inheriti® Tutorials: Setting Up Safe and Encrypted Data Backup Plans
As part of our ongoing commitment to user empowerment and data security, this month’s tutorials—“Create a Free Data Backup Plan with SafeKey Mobile” and “Create a Data Backup Plan with SafeKey Mobile | Standard Mode”—provided a comprehensive walkthrough of the Inheriti® platform’s backup plan creation process. Each tutorial guide users through the six-step procedure, beginning with secure access via inheriti.com using Safe ID credentials. Key steps include entering plan details, designating shareholders (with the free plan assigning the creator as the sole shareholder and merge authority), selecting storage methods, configuring customizable merge triggers, and securely adding sensitive asset data. The final step involves a thorough review before the plan is initialized and shares are securely distributed. Users are reminded to avoid entering secret data in unencrypted fields such as private notes and asset descriptions. Once created, shares are available via the SafeKey mobile application and can be monitored through the plan details section. These tutorials are designed to streamline secure backup creation and enhance user confidence in managing sensitive information.
Exploring the Future of Cybersecurity: Inheriti® at Cybersec Europe 2025
Our team will be attending Cybersec Europe, a premier event for cybersecurity professionals, set to take place on 21-22 May 2025 in Brussels, Belgium. This event promises a high-caliber program, featuring inspiring keynotes, talk shows, Q&A sessions, interactive workshops, and webinars, alongside an exhibition floor showcasing the latest solutions and innovations in the field. For Inheriti®, participating in Cybersec Europe 2025 offers a unique opportunity to present our decentralized approach to digital inheritance and demonstrate how it addresses critical cybersecurity challenges. By providing a secure platform, Inheriti® is committed to enhancing the security and privacy of both individuals and organizations in the rapidly evolving digital landscape.

Inheriti® Demos
Our live Inheriti® demos are in full motion, offering the community a hands-on look at how we are making digital inheritance both secure and seamless. These interactive sessions highlight Inheriti®’s decentralized approach to safeguarding and transferring digital assets while ensuring complete privacy and control.
Your continued support motivates us to enhance our secure, decentralized technology. We’re planning even more demos to showcase the latest advancements in digital legacy planning—stay tuned! We offer demos in both English and Dutch. Feel free to reach out on our socials (x.com) and Telegram, and we’ll be happy to arrange your personal demo.
Community
Some projects make noise.@SafeHavenio BUILDS quietly — real tools, real protection, real future.
I’m tired of watching greatness go unnoticed.
If you believe crypto is about freedom AND security, $SHA is the hidden gem.
Let’s make some noise. #CryptoGems— Craig Worswick (@CraigWorswick) April 27, 2025
@danawhite as #VeChain advisor 👉 you're kin 😁to @safehavenio $SHA 👉engineers for #VeChain infrastructure + Sr. Sec/Net engineer for EU Parliament.
Have patented flagship #RWA product https://t.co/oo4t96zqKS 👉Secure Digital life.@scottmelker #BTChttps://t.co/52DOxKCAH9 pic.twitter.com/WvQ1t5lmpb— JustInTimeMessenger (@JustInTimeMsngr) April 30, 2025
@DefiTokyo your friend got robbed for $3M $BTC needs https://t.co/oo4t96zqKS
Patented, secures digital assets, backups, Digital Inheritance, RED4SEC cert, Dead Man switch for trusted delegates-backup for keys/other #RWA
+Quantum proof 👉 https://t.co/ms2M0fjFU3$SHA #BTC $XRP
— JustInTimeMessenger (@JustInTimeMsngr) April 21, 2025
Back to news

 Nederlands
Nederlands Deutsch
Deutsch Français
Français